Features
Just a few reasons to use RpcView
Exploring the RPC landscape
Most of existing RPC monitoring tools are based on the EndpointMapper system component in order to enumerate all registered interfaces. Nevertheless, many software use RPC with unregistered interfaces as IPC mechanism. In this sense, requesting the EndpointMapper is not a perfect method to enumerate local RPC interfaces. Based on the RPC runtime internals, RpcView is not only able to analyse all interfaces present on a system but is also able to decompile most of them.
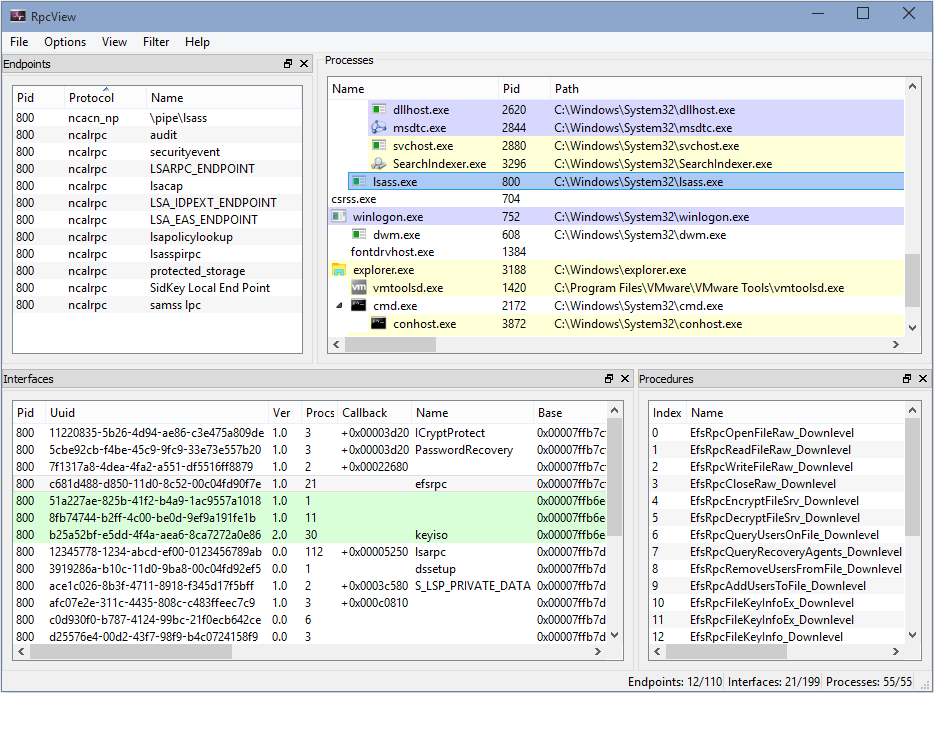
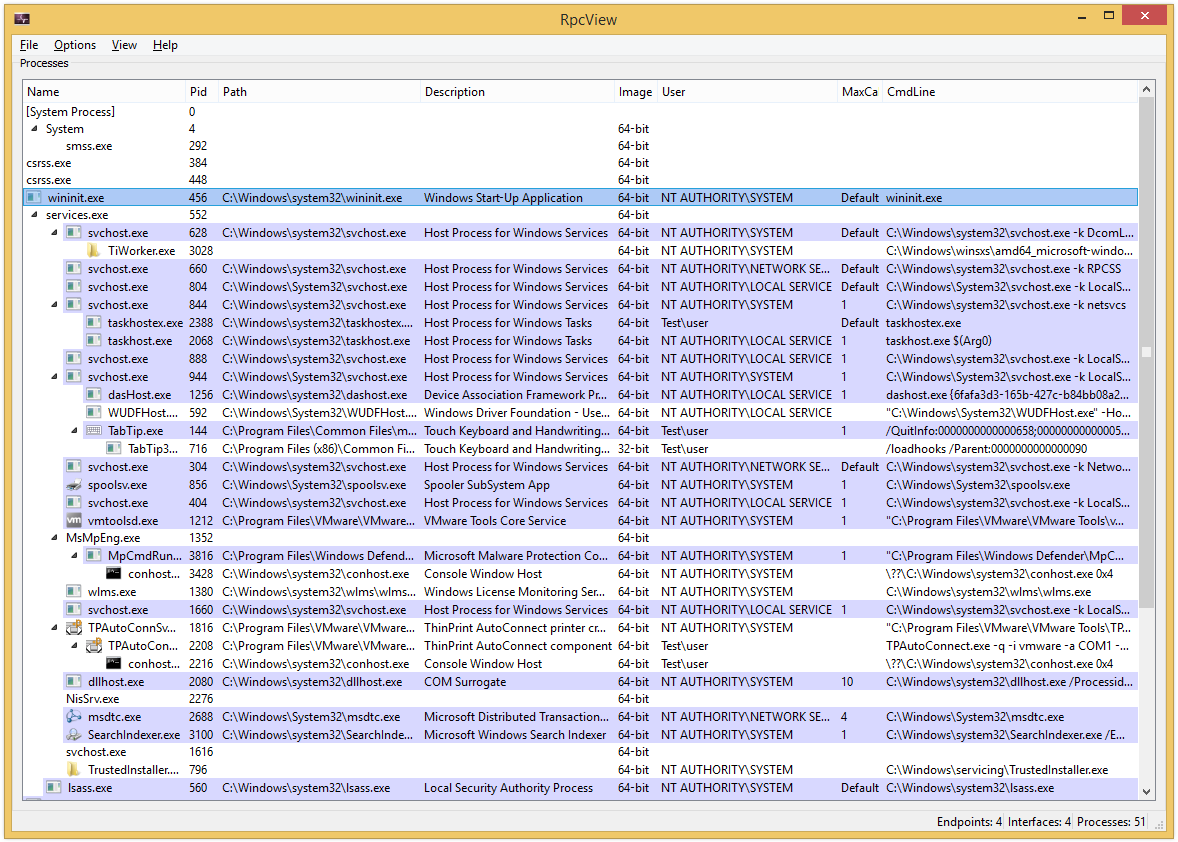
- Name
- Identifiant (Pid)
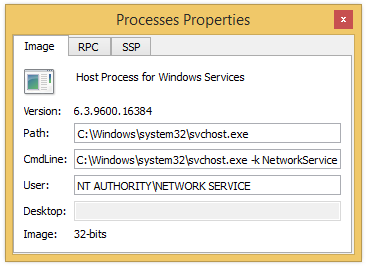
- Path
- Description
- Type of image
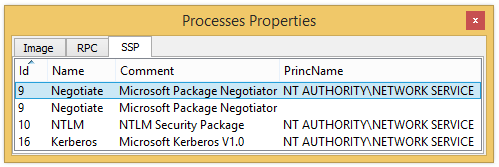
- User
- Command line
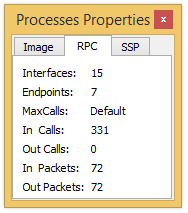
- MaxCalls
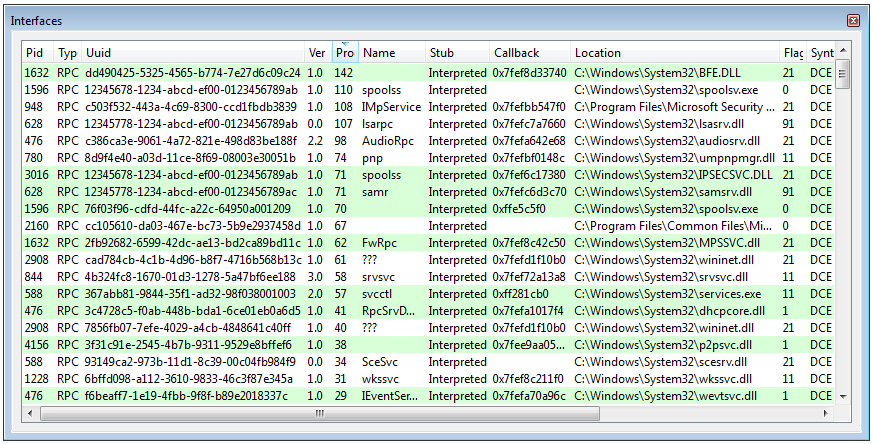
- Pid
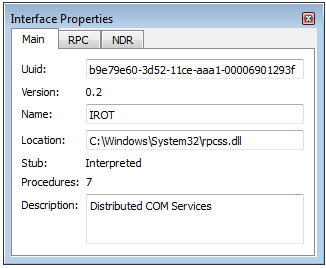
- UIID
- Version
- Type
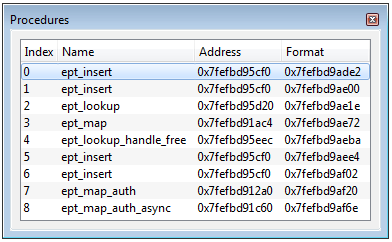
- Number of procedures
- Name
- Type of stub
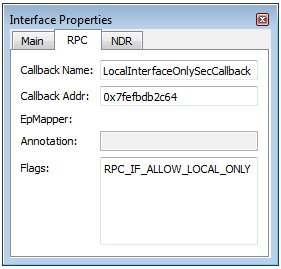
- Security callback address
- Procedures location
- Flags
- Module description
- EpMapper
- Annotation
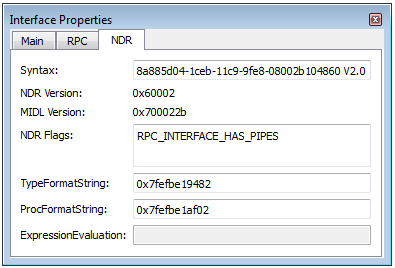
- Transfert Syntax
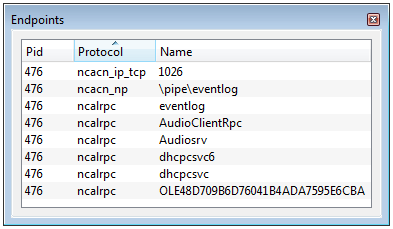
- the Pid of the process hosting this endpoint;
- the used protocol among which the main ones are ncacn_ip_tcp, ncacn_np and ncalrpc;
- the endpoint name depending of the underlying protocol:
- port value for ncacn_ip_tcp or ncadg_ip_udp
- pipe name prefixed by \pipe\ for ncacn_np
- (A)LPC port name for ncalrpc
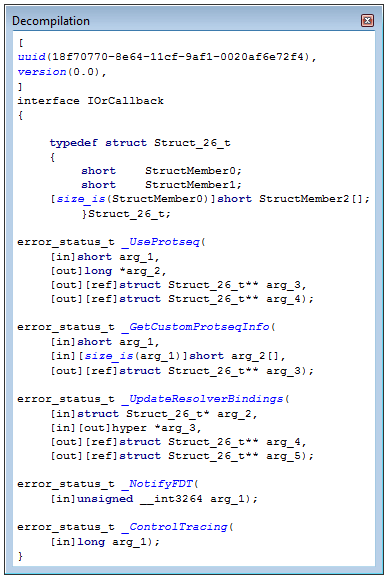
Decompilation
The Microsoft NDR specification allows the decompilation of server stub in charge of the marshalling process. RpcView is able to reconstruct a MIDL compatible IDL file describing an interface.